Secure RemoteIoT On Mac Behind A Firewall
Are you struggling to harness the full potential of your remote IoT devices, especially when navigating the complexities of firewalls and network security on your Mac? Mastering remote IoT connectivity doesn't have to be a daunting task. This comprehensive guide provides clear, actionable strategies to optimize your setup and unlock the seamless control you desire.
The Internet of Things (IoT) has revolutionized how we interact with technology, from smart homes to industrial automation. However, ensuring secure and reliable remote access to these devices can present significant challenges, particularly when firewalls and network configurations come into play. For Mac users, this can seem even more complex, often involving a maze of settings and technical jargon. But fear not, achieving secure and robust remote IoT connectivity on your Mac is entirely achievable with the right approach.
| Topic | Remote IoT Security and Connectivity on macOS |
|---|---|
| Key Concepts | Firewall Configuration, SSH Tunneling, Port Forwarding Alternatives, Network Security Best Practices |
| Relevant Technologies | macOS, Remote IoT Platforms (e.g., AWS IoT), SSH, Routers, Firewalls |
| Target Audience | Mac users managing smart home devices, remote sensors, or industrial IoT systems seeking to enhance security and functionality. |
| Reference | AWS IoT |
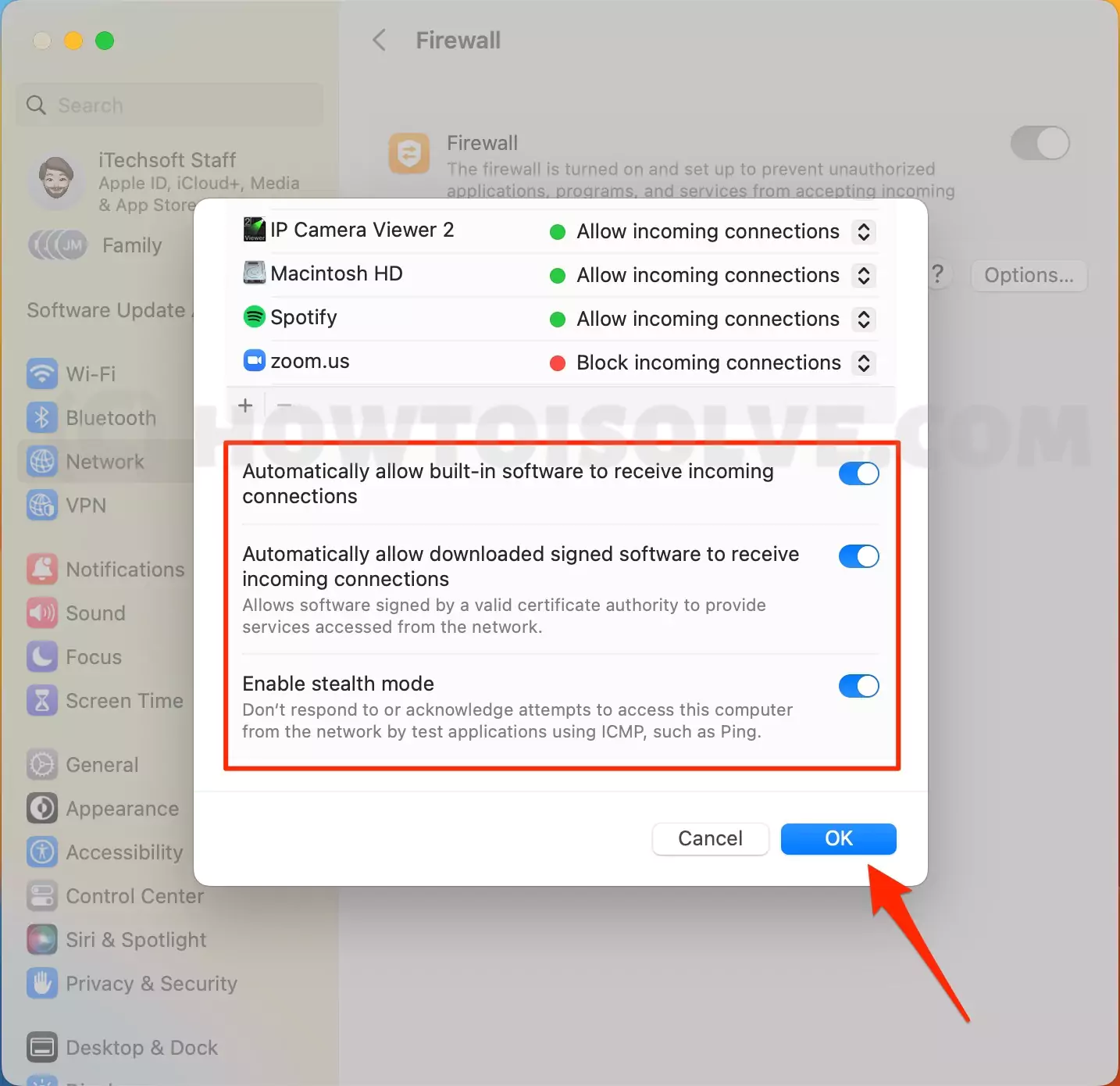
One of the most common hurdles is configuring your firewall correctly. Adding your remote IoT application to your firewall's allowed list is a crucial first step. To do this, access your System Preferences, navigate to Security & Privacy, and unlock the settings. Click the "+" button to add a new app, locate your remote IoT application, and ensure it's permitted to receive incoming connections. This allows your Mac to communicate with your IoT devices without interference.
For users seeking more advanced security, establishing an SSH tunnel provides a robust solution. SSH creates an encrypted connection between your Mac and your IoT devices, safeguarding your data from prying eyes. Using the Terminal on your Mac, you can establish an SSH tunnel to your remote IoT server, ensuring all communication is securely encrypted. This is especially valuable when operating in public networks or managing sensitive IoT data.
Dealing with router restrictions, particularly MAC address filtering and port forwarding, can be another significant challenge. However, there are effective workarounds. While MAC address filtering enhances network security by limiting which devices can connect to your router, it can also hinder remote IoT access. Instead of relying on MAC address filtering, consider implementing stronger password protection and network encryption protocols like WPA3. This offers a more robust security approach without limiting device accessibility.
Many users grapple with port forwarding, a technique that directs incoming network traffic on specific ports to designated devices within your network. However, this can be complex to configure and potentially introduce security vulnerabilities. Instead, explore alternatives like UPnP (Universal Plug and Play) or NAT-PMP (NAT Port Mapping Protocol). These protocols allow devices to automatically request and receive port mappings from your router, simplifying the process and minimizing manual configuration.
Beyond these specific solutions, several best practices can significantly enhance the security and functionality of your remote IoT setup. Segmenting your network by separating your IoT devices from other network devices is crucial. This creates an isolated environment for your IoT devices, reducing the potential impact of security breaches. If one IoT device is compromised, the rest of your network remains protected.
Regularly updating your IoT device firmware is another fundamental practice. Firmware updates often include crucial security patches and performance improvements. Failing to update your devices leaves them vulnerable to known exploits, potentially compromising your entire network. Consider enabling automatic updates whenever possible to ensure your devices are always running the latest, most secure software.
Choosing strong, unique passwords for both your IoT devices and your router is essential. Avoid using default passwords, as these are easily guessed by attackers. Implement multi-factor authentication (MFA) whenever available, adding an extra layer of security by requiring multiple forms of verification to access your devices. This makes it significantly more difficult for unauthorized users to gain control, even if they manage to obtain your password.
Finally, consider leveraging cloud-based IoT platforms like AWS IoT. These platforms provide robust security features, scalable infrastructure, and a range of tools to manage your IoT devices effectively. They also offer enhanced remote access capabilities, allowing you to control and monitor your devices from anywhere with an internet connection.
By understanding and implementing these strategies, you can transform your remote IoT experience on your Mac. From basic firewall configurations to advanced SSH tunneling and cloud integration, these techniques empower you to navigate the complexities of network security, unlock the full potential of your IoT devices, and enjoy seamless, secure control from anywhere.
Securing your IoT ecosystem is a continuous process, requiring vigilance and adaptation to emerging threats. Stay informed about the latest security best practices and update your configurations accordingly. By prioritizing security and implementing these strategies, you can confidently embrace the power of the Internet of Things, knowing your devices and data are well-protected.