Secure Raspberry Pi Remote Access With SSH Tunneling
In today's interconnected world, how can you ensure the security of your home network and devices like the Raspberry Pi? Building your own secure access solutions, rather than relying on third-party VPN providers, offers greater control and potentially stronger security. This approach allows you to tailor your security measures to your specific needs and avoid potential vulnerabilities associated with third-party services.
Many IT professionals express concerns about the trustworthiness of third-party VPN providers. Setting up port forwarding on your home modem, with internal IPs pointing to your Raspberry Pi and external IPs to your server, offers a more direct and potentially safer alternative. This method bypasses the need for a third-party VPN and gives you full control over the connection. For those behind CGNAT, alternative solutions are crucial, and a self-hosted approach provides the necessary flexibility.
| Information | Details |
| Topic | Secure Remote Access to Raspberry Pi |
| Methods | Port Forwarding, Reverse SSH Tunneling, piVPN, Cloudflare Tunnel |
| Security Considerations | Strong passwords, 2FA, Secure SSH and VNC configurations, Regular updates |
| Tools/Software | OpenVPN, WireGuard, Docker, Pi-hole, rpi-monitor |
| Reference | https://www.raspberrypi.com/ |
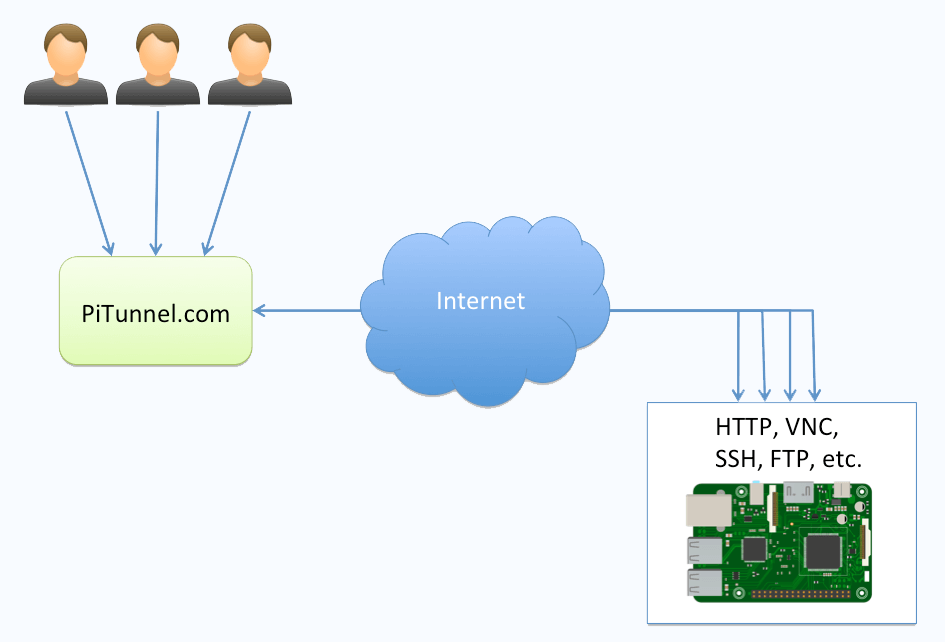
Pitunnel.com presents itself as a highly trusted platform for creating secure tunnels, boasting a high safety score and user trust. While independent user reviews are still developing, the platform offers features like secure remote terminal access, live monitoring of vital Raspberry Pi information, and remote access to TCP servers running on the device. It also facilitates secure sharing of projects with friends and family via tunnel URLs.
However, security best practices remain paramount. When creating custom tunnels, prioritize securing services running behind them by avoiding default usernames and passwords for SSH and VNC. The global accessibility of these tunnels necessitates strong, unique passwords to restrict access to trusted individuals.
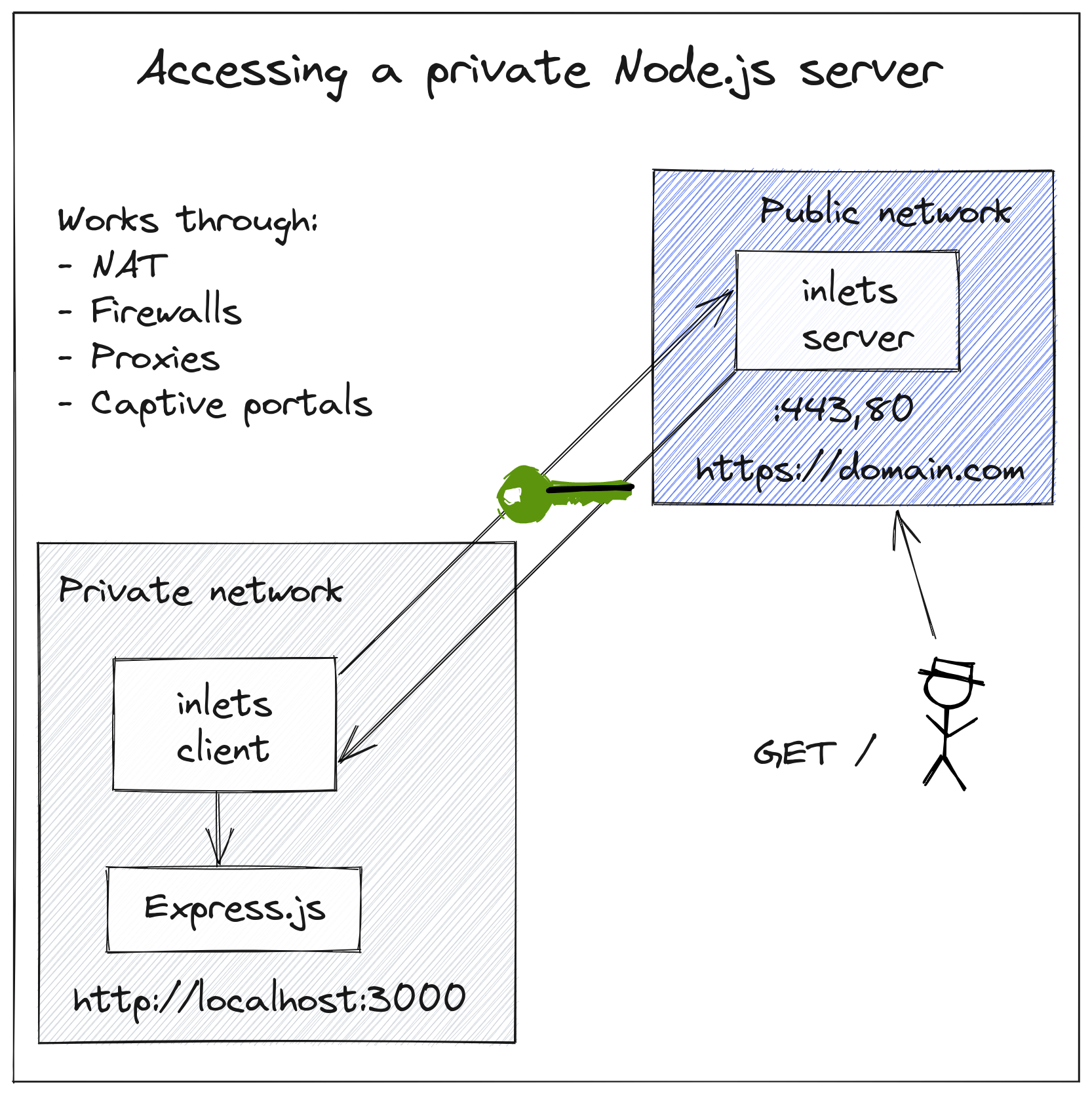
Raspberry Pi Tunnel SSH provides a robust guide to secure remote access. This involves establishing a secure communication channel between your Raspberry Pi and another device over the internet. The process includes enabling SSH on the Raspberry Pi, selecting an appropriate SSH client, and establishing a secure connection. Services like Cloudflare Tunnel offer additional layers of security by mitigating public exposure while enabling content publishing.
Version compatibility is critical. If using the secure tunneling local proxy as the client, ensure both the component and the local proxy are updated to compatible versions (e.g., 3.1.1 or later) to maintain a secure connection.
Securing a Raspberry Pi mirrors securing any Linux device. Regular updates, strong passwords, and disabling unnecessary services are essential. Configuring DNS settings, such as setting the DNS in your Private Internet Access (PIA) on your PC to the Pi's address, can enhance privacy and control. Understanding how VPNs functioncreating a tunnel from your router to a VPN serverhelps clarify how a Pi can fit into this scenario. While a VPN establishes a connection to a chosen location, understanding how DNS settings interact with this tunnel provides a more complete picture.
A secure reverse SSH tunnel offers a cryptographic method for remote Raspberry Pi access, creating an encrypted communication channel between two networks. This is especially beneficial when the Raspberry Pi sits behind a firewall or NAT. Prioritizing security depends on the Pi's function. A Pi controlling home security systems demands heightened security, while a network-isolated gaming Pi poses less risk. This risk assessment helps prioritize security efforts.
Using a VPN adds another layer of security by encrypting data transmitted to and from the Raspberry Pi, shielding online activities from prying eyes. This encryption is crucial for protecting projects and data. Comprehensive guides offer in-depth explanations of SSH setup, configuration, and security for remote access. Creating a custom tunnel for remote SSH access involves enabling SSH and establishing a connection through platforms like pitunnel.com using a unique identifier. This allows access via an address like pitunnel.com:12345. Custom tunnels are created via terminal commands on the Raspberry Pi.
Some criticisms directed at tunnels often stem from concerns about the underlying services they utilize, such as Cloudflare, regardless of whether the transit occurs over a tunnel. Creating a secure tunnel involves generating a unique identifier. Specifying the local service to expose, such as a WordPress instance running on the Raspberry Pi, requires careful configuration. Replacing placeholder domain names (e.g., mydomain.com) with your actual domain and ensuring the service is running are critical steps. Starting the tunnel requires specific commands.
Accessing Home Assistant through a Cloudflare Tunnel, even with strong passwords and 2FA enabled, raises security questions about the login page. Failed login attempts, while potentially harmless service connection failures, could also indicate hacking attempts. Analyzing website traffic and optimizing website experience through cookies is common practice but should be transparent to users. Pi VPN, a lightweight OpenVPN server designed for Raspberry Pi 2 or 3, enables secure access to your home network over the internet.
Building a robust home network often involves combining multiple tools. Using piVPN (OpenVPN or WireGuard) allows VPN access into your network. Port forwarding to your Pi's IP address enables external access to specific services. Scripts to install Docker on the Pi unlock extensive functionalities. Installing Pi-hole as your default DNS provides network-wide ad blocking and improved privacy. However, be mindful of software conflicts; for instance, installing Portainer from DietPi might conflict with Pi-hole.